Specs and Terminal Diagram
Hardware Diagram

- *A
- SMA connector
- *B
- Status LED
- *C
- Serial Number
- RESET
- Reboot the Noi gateway
- MODE
- Used in advanced troubleshooting cases, can put the Noi gateway into safe mode.
- POWER INPUT
- Main voltage source for the Noi gateway
- OPTO ISOLATED IO
- DI
- Inputs or triggers
- DO
- Outputs or switches
- DI
Maximum and Minimum Ratings
There are 2 models of NOI that have been manufactured to date. The main difference between them is a simple change of the input voltage range that they can accomodate. Any device that was purchased and shipped after August of 2022 will be model NCG-2. Please pay attention to the different input voltage requirements listed on both this page and the hardware itself.
Input Voltage
Warning
Please verify the model of your NOI by checking the input voltage range listed above the power terminals. Model NCG-2 has a reduced voltage range and you can easily damage it by giving it a higher voltage.
- Model
NCG-2: 12-24VDC Nominal (10-48VDC Literal) - Legacy Model
NCG-1: 12-48VDC Nominal (10-72VDC Literal)
Power Consumption
- Minimum of 1 Watt required, 1.5W recommended
- 350mW resting (local communications)
- 1.2W when publishing data (cellular communications)
Temperature Range
- -40°C to +85°C
SMA Connector
- Impedence
- 50 ohms
Opto Isolated IO
- Supply Voltage
- 5-48VDC Nominal
- Output Current
- 850mA
Temperature Probe
- Sensor Interface
- DS18B20 OneWire
- Datasheet
- Output Voltage
- 3.3V
- Maximum Output Current
- 500mA
Warning
Pulling more than 500mA through the temperature probe can damage the power supply for the processor, effectively rendering your Noi gateway useless. Please limit yourself to powering a single DS18B20 from these terminals.
Cell Module
Connexa uses an integrated and preapproved module manufactured by Particle. Following are the links to the spec sheets and certifications.
4G LTE
- U-Blox SARA-R410M
- FCC Certifications
- PTCRB
2G/3G
- U-blox SARA-U201
- FCC Certifications
- PTCRB
Processor
- Arm® Cortex®-M3 32-bit RISC
Security
Device to Cloud security is managed by Particle. Much of the following information comes directly from their white paper "Security Checklist for the Internet of Things".
Communications Protocol Security
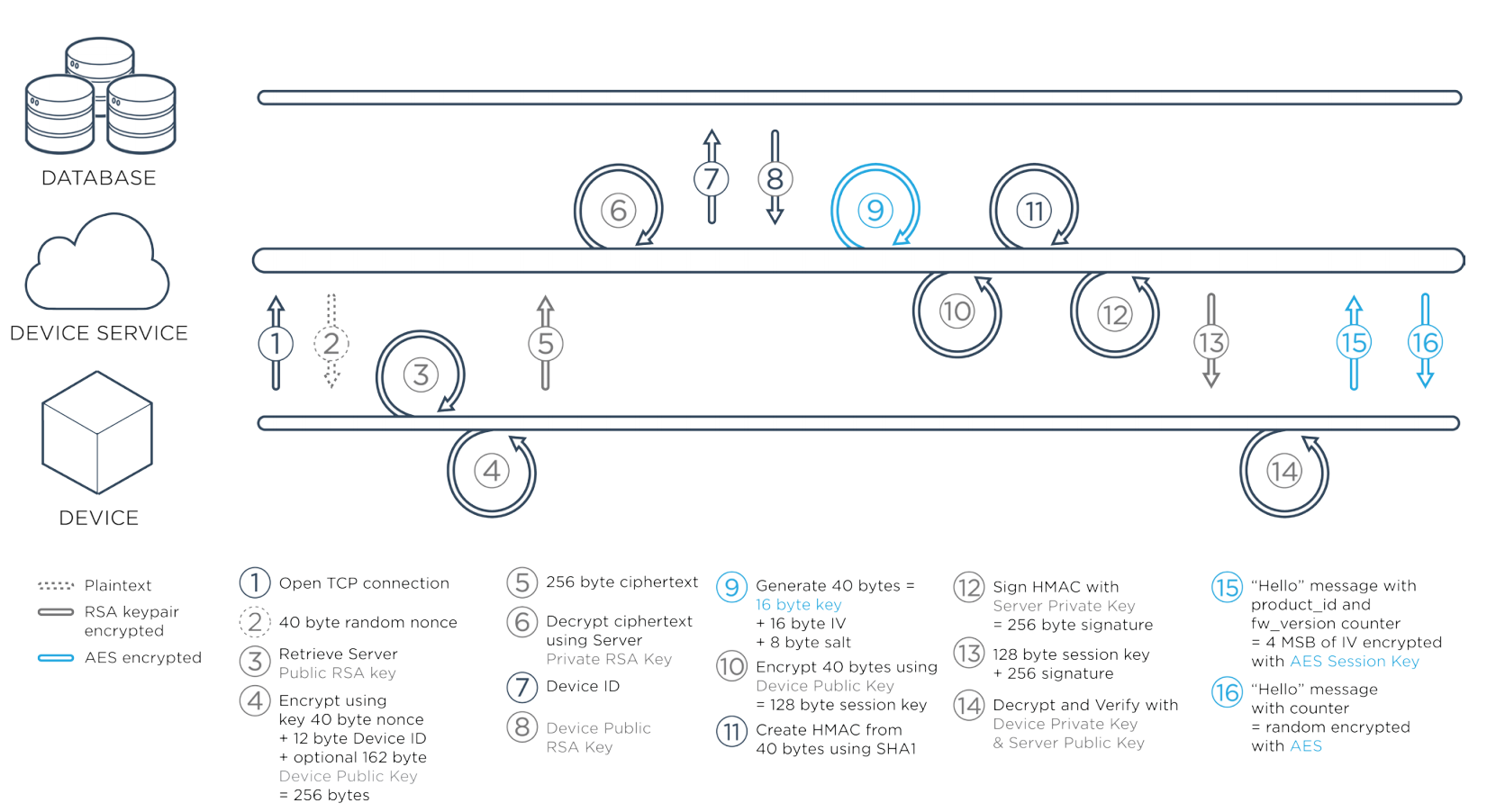
Above is a diagram of the TCP connection handshake that instantiates a cloud session. Every device ships with a unique device-specific RSA or Elliptic Curve key-pair, and has a pinned Cloud public key. The device public key is typically pinned in the cloud during manufacturing, but can be updated later by an authorized user.
Particle’s TCP service uses an RSA handshake to establish a session key for a fast rotating AES-128-CBC session. Each message is encrypted and is checked via a message id for replay attacks or out-of-order messages. Any anomaly in the session causes it to immediately end. Although all Particle devices include hardware random number generators, the RSA/AES cloud handshake includes a cryptographically random nonce, to ensure there is sufficient randomness on these low-power devices.
Particle’s UDP service uses DTLS. 256 bit ECC keys are used for the DTLS service, roughly equivalent to a 3072-bit RSA key.
OTA Updates
The device is also protected against failures during the Over The Air (OTA) firmware update process. Each firmware module includes a verifiable hash and metadata to ensure the code is appropriate for that platform and product. If a corrupted firmware is sent to a device, or a mismatched firmware for that product, the device will safely fall back to the last known good firmware stored locally in flash.